SQL Injection
SQL injection is a method of attacking a website that involves of the insertion or "injection" of an SQL query via input data from a client, such as a Web browser, to a Web application that interacts with a database.
SQL injection attacks are a type of injection attack, in which SQL commands are injected into inadequately filtered / sanitized input in order to effect the execution of predefined SQL commands.
A successful SQL injection attack can get sensitive data from a database, modify database data and execute administration operations on the database including shutting the down the database server and in some cases execute commands on the the operating system.
SQL injection attacks enable attackers to become administrators of a database server, at which point they can easily extract, modify, disclose and / or destroy any and all data on the system, as well as modify user accounts.
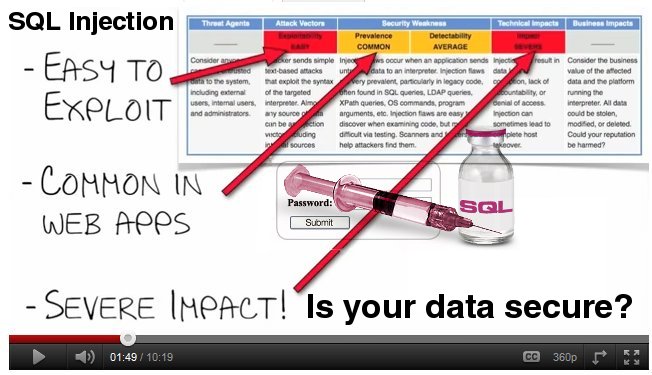
SQL Injection is very common with PHP and ASP applications due to the prevalence of legacy code with which older functional interfaces were created with.
ASP.NET applications are less likely to be vulnerable to SQL injections because of the use programmatic interfaces which act as a barrier when communicating with the database server.
The severity of SQL Injection attacks is only limited by an attacker’s skill and imagination, and to a lesser extent, defensive countermeasures, such as low privilege connections to the database server and so on.
Generally speaking, damage from SQL Injection is a high impact severity.
SQL Injection exploits occur when:
A web application accepts data from an untrusted source without properly escaping or replacing potentially damaging input. The data is used to dynamically construct SQL queries.
The consequences of a SQL Injection Exploit are often severe and can completely disrupt or disable an organization's functionality. Some of the direct consequences of SQL Injection are:
Loss of Confidentiality: Since SQL databases generally hold sensitive data, including personal and financial information, loss of confidentiality is significant problem with SQL Injection vulnerabilities.
Data Integrity: Just as it is possible to read sensitive information, it is also possible to make changes or even delete this information with SQL Injection attacks.
Authentication and Authorization: If poor SQL commands are used to check user names and passwords, it is possible to login in to a website as another user with no previous knowledge of the password.
SQL Injection has become a common issue with database driven web sites. The flaw is easily detected, and easily exploited, and as such, any site or software package with even a small user base is likely to be subject to an attempted attack of this kind.
SQL Injection attacks are accomplished by inserting a meta character into a web application's data input, then appending SQL commands which are designed to compromise the integrity of a web application's functionality.
Conventional security measures, such as the use of Secure Socket Layer (SSL) do not protect your application from SQL injection attacks.
A successful SQL injection attack enables a malicious user to execute commands in your application's database by using the privileges granted to your application's login. The problem is more severe if your application uses an over-privileged account to connect to the database.
For example, if your application's login has privileges to delete a database, then without adequate safeguards, an attacker might be able to perform this operation.
Common vulnerabilities that make your web application's data access functions susceptible to SQL injection attacks include:
- Weak input validation.
- Dynamic construction of SQL statements without the use of type safe parameters.
- Use of over-privileged database logins.
DATABASE
database security