Healthcare companies integrating new patient management systems are encountering significant security and compliance hurdles, driven by a surge in ransomware attacks, the need to comply with tightening 2025–2026 HIPAA modifications, and the complexities of integrating modern systems with legacy infrastructure. As organizations transition to cloud-based systems and advanced AI, they face critical vulnerabilities, including weak vendor security, fragmented identity management, and increased human error, often leading to costly data breaches and disrupted patient care.
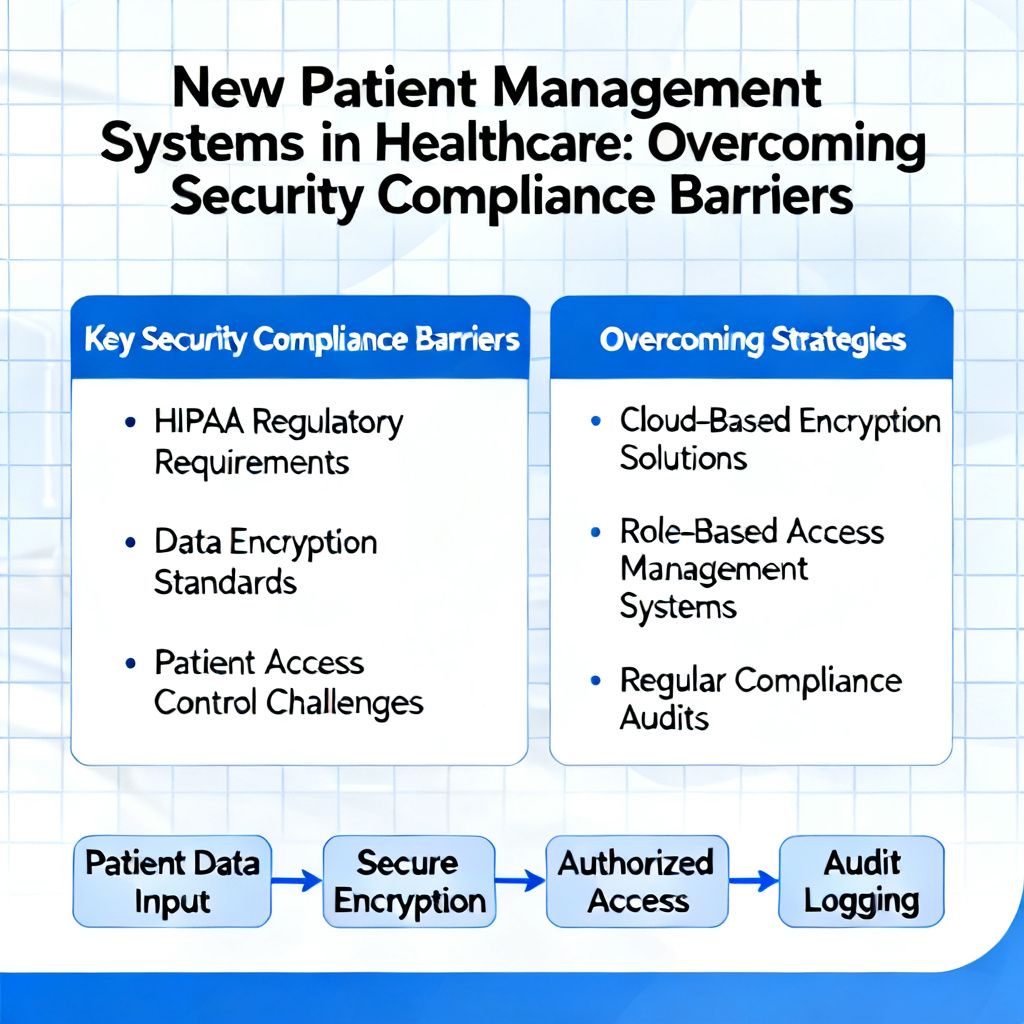
Key Security and Compliance Challenges
2025–2026 HIPAA Updates and New Regulations: The U.S. Department of Health and Human Services (HHS) is expected to overhaul the HIPAA Security Rule by May 2026, moving from “addressable” controls to mandatory requirements, such as mandatory Multi-Factor Authentication (MFA) and faster, 72-hour breach reporting.
Legacy System Integration: Many healthcare organizations rely on older systems not designed with modern security protocols, creating vulnerabilities when connected to new, cloud-based patient management platforms. Attempting to integrate new patient systems with outdated technology often creates fragmented, insecure infrastructures. The shift toward new, often cloud-based, systems aims to improve patient care but frequently introduces vulnerabilities, such as gaps in legacy system integration, that can result in regulatory fines, with non-compliance penalties ranging from $100 to $50,000 per violation.
Third-Party and Vendor Risk: The reliance on external vendors for IT and administrative services creates, which, if not properly vetted, can introduce, significant, security vulnerabilities which can resul in massive patient data exposure. Nearly 59% of healthcare breaches involve third-party vendors, making supply chain security a critical, high-cost vulnerability.
Compliance Complexity (HIPAA/HITECH): Organizations are struggling with “framework overload,” trying to map HIPAA, NIST, and state regulations to new, often cloud-based, systems. New systems must adhere to evolving, strict data protection standards, including upcoming requirements for multifactor authentication (MFA) and enhanced encryption.
Inadequate Access Control: Many breaches are linked to improper “shadow AI” or “shadow IT” (unapproved tools) and poor Role-Based Access Control (RBAC), leaving sensitive data exposed.
Endpoint and Device Vulnerabilities: The proliferation of Internet of Medical Things (IoMT) devices and remote working, which often lack robust security, increases the attack surface.
Human Error: Despite technology advancements, human factors remain a primary weakness, with staff under pressure being more susceptible to phishing and data mishandling.
Resource Constraints: Limited budgets and staff specialized in both IT and healthcare regulations can delay crucial security updates and audits.
Common Pitfalls and Consequences
Fragmented Systems: Relying on disconnected tools and spreadsheets leaves patient information vulnerable.
Delayed Compliance: Delaying compliance efforts to save costs often leads to much higher expenses related to fines and breach remediation.
Data Vulnerabilities: Inadequate security during cloud migration or in AI tools (e.g., “shadow AI”) increases the likelihood of breaches, with 97% of organizations experiencing AI-related security incidents lacking proper access controls.
Risks Associated with Non-Compliance
Financial and Reputational Damage: Non-compliance fines can range from $100 to $50,000 per violation, with total breaches costing organizations millions of dollars.
Patient Safety and Operational Disruption: Ransomware attacks can paralyze patient management systems, leading to canceled surgeries and diverted ambulances.
Regulatory Scrutiny: Increased enforcement, including mandatory annual risk assessments and tighter data protection, means that “check-the-box” compliance is no longer sufficient.
Financial Impact and Costs
The financial strain of these issues is substantial and multifaceted.
Healthcare companies in 2026 are aggressively modernizing patient management systems to improve care, yet they face severe financial and operational hurdles stemming from security breaches and complex regulatory compliance. The average cost of a healthcare data breach in the U.S. reached $7.42 million to $10.22 million per incident in 2025, the highest of any industry for the 14th consecutive year. These costs, often driven by ransomware and third-party vendor breaches, now significantly impact operating margins, with IT compliance expenses consuming approximately 6% of Medicare reimbursements.
High Breach Costs: Beyond the average $10M+ cost, breaches take an average of 279 days to identify and contain, leading to massive disruptions.
Regulatory Penalties: HIPAA violations can result in fines ranging from $100 to $50,000 per violation.
Operational Strain: Many organizations are forced to hike prices—with roughly one-third increasing them by 15% or more to cover the cost of breaches.
In 2024, one organization faced a $1.5 million fine, plus $500,000 in remediation, totaling $2 million for a single incident.
Compliance Implementation Costs: Implementing necessary security measures for medium-to-large organizations averages $80,000, while total HIPAA compliance can exceed $100,000 for large enterprises.
Operational Downtime: Data breaches can halt operations, with costs estimated at up to $9,000 per minute for some healthcare organizations due to system downtime.
Projected Spending: New, stricter data security regulations could cost the industry up to $9 billion in the first year to implement.
Strategic Responses
To mitigate these costs, healthcare organizations are adopting several strategies:
Proactive Security Spending: Moving from reactive, “box-ticking” compliance to automated GRC (Governance, Risk, and Compliance) tools to continuously monitor vulnerabilities.
Zero Trust Architecture: Implementing stricter, identity-based security rather than relying on perimeter defenses.
Vendor Risk Management: Tightening Business Associate Agreements (BAAs) and conducting regular, rigorous security audits on partners.
AI for Defense: While AI is a source of risk, its use in security analytics is helping to reduce breach lifecycles and lower costs.
Mitigation Strategies
To address these challenges, healthcare organizations are advised to:
Adopt Proactive Security: Utilize automated compliance platforms and continuous monitoring to detect vulnerabilities before they are exploited.
Adopting Zero Trust Architectures: Implementing strict identity verification for every user and device trying to access resources, regardless of whether they are sitting within or outside of the network perimeter.
Automating Compliance and Risk Management: Using tools to automate, third-party risk assessments, continuous monitoring, and policy updates.
Conduct Regular Audits: Perform vulnerability scanning at least every six months and penetration testing annually.
Invest in Regular Staff Security Training: Ensure staff are trained on new, secure data handling procedures. Continuous education for staff to recognize, phishing and adhere to data protection protocols.
Strengthening Vendor Management: Ensuring Business Associate Agreements (BAAs) include strict security requirements, such as encryption and MFA, and verifying these, annually.
Leverage Standards: Use established standards like SMART on FHIR for secure data exchange.
Example of using SMART on FHIR for secure data exchange in C++
#include <iostream>
#include <string>
#include <curl/curl.h>
// Helper to store response data
size_t WriteCallback(void* contents, size_t size, size_t nmemb, std::string* userp) {
userp->append((char*)contents, size * nmemb);
return size * nmemb;
}
int main() {
CURL* curl = curl_easy_init();
if (!curl) return 1;
std::string response_data;
std::string fhir_url = "https://fhir-server.example.com/r4/Patient/123";
std::string access_token = "YOUR_SMART_ACCESS_TOKEN"; // Retreived from SMART Launch
// 1. Set the FHIR endpoint URL
curl_easy_setopt(curl, CURLOPT_URL, fhir_url.c_str());
// 2. Add Authorization and Accept headers
struct curl_slist* headers = NULL;
std::string auth_header = "Authorization: Bearer " + access_token;
headers = curl_slist_append(headers, auth_header.c_str());
headers = curl_slist_append(headers, "Accept: application/fhir+json");
curl_easy_setopt(curl, CURLOPT_HTTPHEADER, headers);
// 3. Configure secure HTTPS options
curl_easy_setopt(curl, CURLOPT_FOLLOWLOCATION, 1L);
curl_easy_setopt(curl, CURLOPT_WRITEFUNCTION, WriteCallback);
curl_easy_setopt(curl, CURLOPT_WRITEDATA, &response_data);
// 4. Perform the request
CURLcode res = curl_easy_perform(curl);
if (res == CURLE_OK) {
std::cout << "FHIR Resource Data: " << response_data << std::endl;
} else {
std::cerr << "Request failed: " << curl_easy_strerror(res) << std::endl;
}
// Cleanup
curl_slist_free_all(headers);
curl_easy_cleanup(curl);
return 0;
}
To obtain an access_token from an EHR provider in C++, you must implement the SMART on FHIR Authorization Code Flow.
std::string post_data =
"grant_type=authorization_code"
"&code=" + auth_code +
"&redirect_uri=http://localhost:8080/callback"
"&client_id=YOUR_CLIENT_ID"
"&code_verifier=" + original_code_verifier; // Required for PKCE
Request a FREE Security and Compliance consultation now.